Trusted Platform Modules (TPMs) and Intel TDX: The Future of Hardware-Based Security

Trusted Platform Modules (TPMs) and Intel® Trust Domain Extensions (TDX) are transforming not only hardware-based security but also cloud servers computing safety.
As the leading confidential computing technologies, TPMs lock down cryptographic keys and verify system integrity, while Intel TDX shields VM in cloud setups, keeping sensitive data safe and secure in shared environments. In combination, they deliver the ultimate security measurements.
As a leader in dedicated and cloud hosting, ServerMania allows you to tap into TPMs and Intel TDX with their server solutions. Whether you’re running critical apps or safeguarding data, ServerMania’s reliable, high-performance architecture makes it simple to deploy these technologies.
We know that grasping these complicated terms may be challenging, so in this guide, we will dive into a TPM and Intel TDX comparison and show you how these technologies boost security. Let’s get started…
What is TPM – Trusted Platform Module?
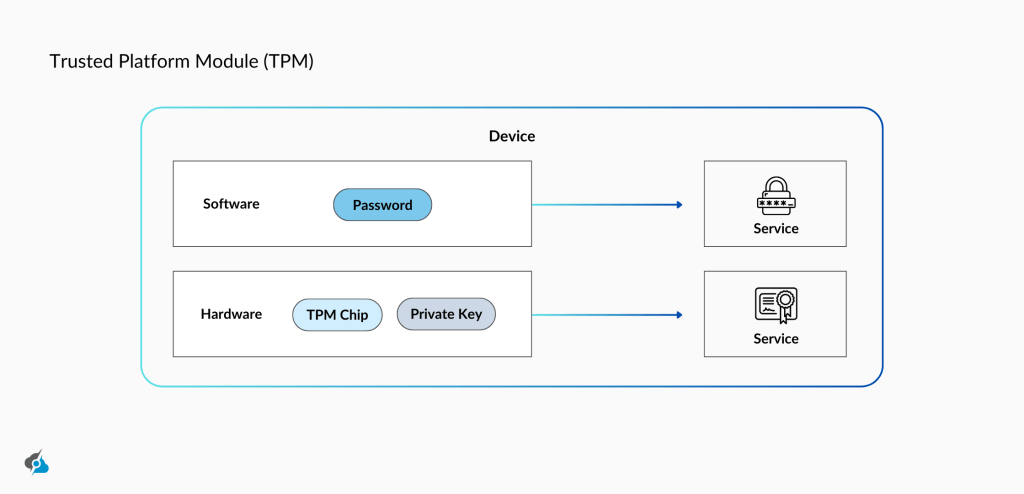
Trusted Platform Module, TPM for short, is a chip built into the Windows computer motherboard, increasing the security. It stores away the so-called “cryptographic keys” that are used for encrypting and decrypting. With each TPM version enhancing these capabilities, this ensures your computer operating system and firmware stay safe and secure.
TPMs come as discrete TPM chips or solutions, like Microsoft’s Pluton, including the TPM functionality by being built into the CPU. This reduces the room for cyber threats by skipping external connections.
Here are some examples of Windows security apps using TPM to enhance security:
- Windows Hello uses TPM to store biometrics such as fingerprints, face scans, and PINs, providing you with a smooth, secure login while restricting access without needing a password.
- BitLocker is solely dependent on TPM to protect your hard drive and to keep your data safe even when your device goes missing, sometimes even requiring physical presence.
There are many more Windows security apps enhanced by TPM, such as Secure Boot, Credential Guard, Device Health Attestation, and more…
Trusted Platform Module – Overview
The Trusted Platform Module (TPM) technology is a game-changer for computer security, delivering hardware-level protection against malware and cyberattacks. It’s a secure crypto processor, either a physical chip or merged into modern CPUs, that locks down sensitive data like passwords, certificates, and fingerprints behind a device-hardware wall.
With Windows 11, Microsoft released TPM 2.0, which is a must-have, pushing this tech from enterprises only to ITs and consumers’ hands. So, by following standards from the Trusted Computing Group (TCG) and ISO/IEC 11889, TPM 2.0 uses cryptography to authenticate platforms and keep your data safe.
Each TPM version builds on this foundation, and TPM 2.0 brings enhanced features like stronger encryption and better platform integrity checks. It’s a small chip with a big job, making security tougher and more accessible than ever.
How Does TPM Chip Work?
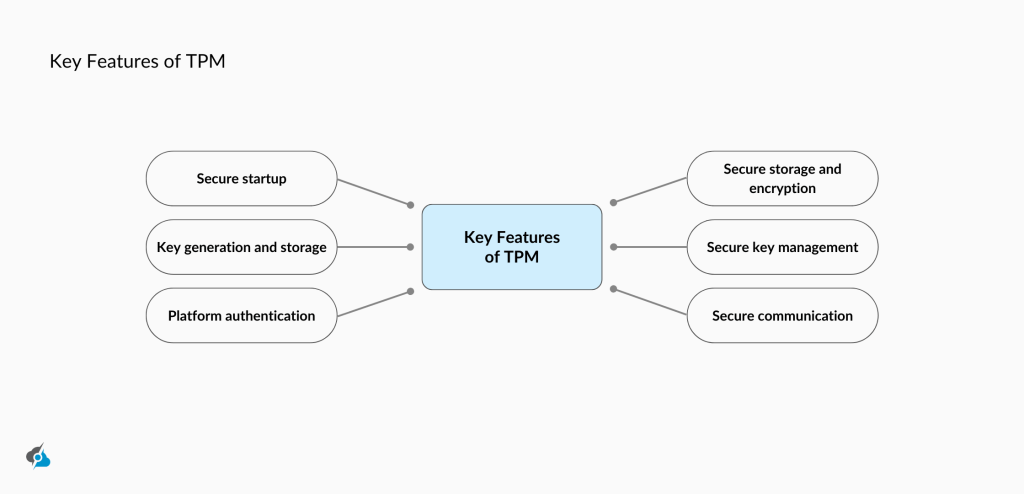
Imagine turning on your computer, and the TPM immediately hops on board to authenticate it, verifying the TPM state for trustworthiness. It generates and stores parts of encryption keys, handing over a cryptographic key and verifying that the firmware hasn’t been tampered with.
There are numerous checks, some of which include whether your Windows device boots up normally, if it’s been altered, or if the device hardware has been replaced.
With cyberattacks getting smarter with AI on the horizon, TPMs are a solid shield for businesses and users alike. Also, to run Windows 11, you’ll need TPM 2.0 compatibility, making it a key piece for staying safe and up-to-date. In short, TPM security is a simple yet powerful way to keep any cyber intruders away.
TPM in Cloud Computing
The Trusted Platform Module technology steps up security in Windows cloud computing by delivering security starting from a device level. In the cloud, where the virtual machines share physical servers, TPMs ensure data confidentiality by checking platform integrity and deploying HW-level encryption.
With Windows 11 computers mandating TPM 2.0, it’s becoming mandatory for cloud setups, offering a solid shield against malware and breaches.
In cloud environments, TPMs stand out by enabling secure boot and remote attestation, controlling access to sensitive workloads. Cloud giants like ServerMania, Google Compute Engine, and AWS have rolled out virtual TPMs (vTPMs), providing assurance that their workloads run on untampered systems.
So, whether you’re protecting sensitive workloads or meeting compliance needs, TPMs reduce the chances of security issues, making them a key player in today’s virtualized cloud world.
Practical Applications of TPM
Trusted Platform Module or (TPM) technology brings hardware-based security to Windows users with real, everyday uses. Here are some examples of TPM in cybersecurity:
- Business Security: Many large-scale companies running Windows, whether they utilize on-premises hosting or cloud, use TPM to protect employee credentials and certificates.
- Cloud Verification: In cloud setups like Google Cloud and Microsoft Azure, TPM ensures that virtual machines boot untampered, building trust for sensitive workloads.
- Virtualization Work: TPM strengthens VPNs and remote access by storing encryption keys and giving users control over off-site connections, reducing the attack surface to a minimum.
- Task Compliance: For regulated fields like healthcare or finance, TPM’s software integrity checks meet tough data protection standards and inspecting unauthorized users.
TPM’s data security and real-world impact are hard to ignore. They cover everything from speeding up logins to safeguarding drives and securing remote work. This revolutionary tech shows hardware-based safety isn’t just a myth, instead, it’s an everyday solution keeping us ahead of potential digital threats.
What is Intel® Trust Domain Extensions (TDX)?
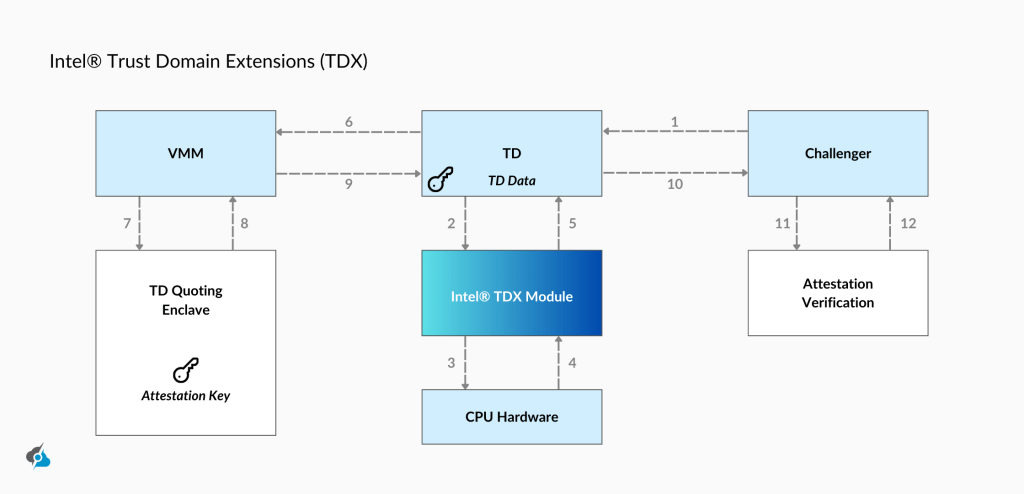
Intel® Trust Domain Extensions (Intel® TDX) is an exciting new tech from Intel that enables the next step in cloud computing security. TDX brings in Trust Domains, also known as TDs (trusted execution environment), which are very secure virtual machines (VMs).
In short, the Intel TDX security keeps sensitive data and apps super safe in shared cloud setups.
Using a CPU-measured Intel TDX module, TDX operates in a Secure Arbitration Mode (SEAM), which leverages existing virtualization infrastructure. Well, this module, hosted in a reserved memory space (SEAMRR), ensures data confidentiality and integrity by encrypting memory and isolating TD CPU states from non-SEAM components, such as the operating system or hypervisor.
TDX is built with architectural elements like Intel® Total Memory Encryption, Multi-Key (TME-MK), Extended Page Tables (EPT), and external attestation. Hence, Intel’s TDX protects virtual machines from underlying hardware and other VMs. Launched with 4th Generation Xeon Scalable Processors in 2023, it’s a giant leap forward for secure, trusted computing in cloud environments.
Intel TDX Explained

Intel Trust Domain Extensions (TDX) brings a fresh twist to cloud computing security in Windows platforms, mixing Multi-Key Total Memory Encryption (MK-TME) and the Intel® Virtual Machine Extensions (VMX) with a TDX Instruction Set Architecture (ISA).
TDX incorporates a few hardware and software components, including:
1. Trust Domain (TD)
A protected, isolated space where a virtual machine’s code, data, and firmware stay protected. Away from the operating system, hypervisor, and other TDs, it keeps everything confidential and safe from unauthorized access.
2. Memory Encryption
The hardware-based encryption locks down a TD’s data in memory. This ensures that even if someone acquires physical access, they can’t read or tweak the encrypted contents, keeping your data protected.
3. TDX Module
The Intel TDX module is the piece that manages Trust Domains, handling setup, state tracking, and software communication while restricting access. All of this happens while staying isolated with limited privileges to avoid unwanted intrusion with the TDs.
4. Measured Boot
A boot process that records cryptographic key measurements of the software stack in secure storage, confirming the software boots in a trusted state and hasn’t been hacked.
5. Remote Attestation
A feature forcing intruders to verify the TD’s integrity with cryptographic evidence, proving it’s running on a legit platform with untampered software.
These elements team up to make TDX a solid solution for securing critical workloads where your data remains secure. So, whether you’re protecting data in the cloud or checking a system’s trustworthiness, TDX delivers safer virtual environments for ultimate peace of mind.
Intel TDX – Advantages
Intel® TDX enables improvement for cloud service providers, enterprise IT teams, and multi-tenant systems tackling virtualized environments.
Here are some of the greatest benefits of Trust Domain Extensions (TDX):
- Security & Isolation: TDX locks Trust Domains (TDs) down with hardware-level isolation, giving providers control over protection and ensuring data confidentiality.
- Remote Attestation: The remote attestation allows you to ensure a TD’s integrity, providing cloud users running important workloads confidence while reaching outside services.
- Full Support for VMs: TDX aligns smoothly and integrates into existing VM setups without major tweaks, making it a no-brainer for cloud providers and enterprises.
These advantages position TDX as the ultimate security tool for anyone with security requirements in the cloud or virtualized spaces. It’s not just about keeping your data locked but also about building trust and flexibility into computers that handle critical workloads, keeping the sensitive data stored safe.
Intel TDX Use Cases
Intel® Trust Domain Extensions (TDX) bring hardware-based security to virtualized environments with many real-world applications. Here’s how TDX can enhance security:
- Cloud Isolation: Intel TDX locks Trust Domains (TDs) away from hypervisors and other VMs, keeping sensitive workloads and application code safe in shared cloud setups.
- Data Protection: With memory encryption, TDX ensures that the device data in TDs stays confidential and blocks unauthorized access even if physical hardware gets compromised.
- Remove Verification: Remote attestation lets cloud users confirm TDs are legitimate, providing trust and transparency for critical apps and external connections.
- Enterprise Security: Companies use TDX to improve virtualized server security, reduce the attack surfaces in multi-tenant device systems, and enable ultimate protection.
- Seamless Integration: Intel TDX fits into existing virtualization infrastructure, making it easy for providers to deploy without big obstacles.
- Regulated Workloads: In fields like finance or healthcare, TDX’s isolation and attestation enable the meeting of strict compliance needs for virtual setups.
So, the practical advantages of TDX are evident. It serves as an easily accessible solution for safe virtualization, effectively addressing security demands by isolating cloud workloads. It ensures trust verification and safeguards regulated data while maintaining virtualization’s integrity and dependability.
Sensitive Data Protection: TPM vs Intel TDX
Trusted Platform Modules (TPMs) and Intel® Trust Domain Extensions (TDX) collaborate to create an ultimate device-based security.
- TPM anchors security at the device level, storing cryptographic keys and checking software integrity from boot-up, ensuring the platform’s trustworthiness.
- TDX builds on this by extending that trust into virtualized environments, isolating Trust Domains (TDs) with device memory encryption across the software stack.
Together, they enable ultimate safety. TPM starts things off by protecting Windows hardware, and then TDX takes over virtualization, locking down VMs and proving their integrity to cloud providers.
For instance, a TPM might validate the server’s boot process, while TDX ensures the virtual workloads running on it stay isolated and untampered. This combo lowers attack surfaces, boosts confidentiality, and makes cloud computing safe, as seen with cloud providers like ServerMania and Microsoft Azure.
Operating System Security With TPM and TDX
TPMs and TDX don’t just protect hardware; they safeguard the operating system, too. TPM ensures the operating system boots untampered by validating its integrity with cryptographic checks, while TDX keeps virtualized operating systems isolated in Trust Domains, safe from external threats.
This duo delivers end-to-end protection across physical and virtual layers.
Intel TDX vs AMD SEV
Intel® Trust Domain Extensions (TDX) and AMD Secure Encrypted Virtualization (SEV) are competitors in hardware-based protection for virtualized environments.
- The Intel TDX, launched with 4th Gen Xeon Scalable processors in 2023, isolates Trust Domains (TDs) using memory encryption and a Secure Arbitration Mode (SEAM).
- In turn, AMD SEV, introduced earlier in 2016 with EPYC processors, encrypts each VM’s memory with unique keys via the AMD Secure Processor, protecting data even if the server is breached.
Hence, while both enhance confidentiality, TDX leans on Intel’s architectural extras like SEAM for robust isolation, whereas SEV’s strength lies in its utilizing encryption simplicity, with upgrades like SEV-SNP adding integrity checks. So, for cloud providers like ServerMania, TDX offers seamless integration with existing virtualization, while SEV appeals to AMD-based systems—two paths to safe, trusted computing.
TPM and TDX Cloud Service Provider – ServerMania!
In summary, Trusted Platform Modules (TPMs) and Intel® Trust Domain Extensions (TDX) collaborate to redesign security for cloud service providers, and ServerMania stands out as a prime example.
With the ServerMania top-tier cloud hosting and dedicated hosting powered by Intel Xeon Servers, you get the best of TPM’s device-level protection and TDX’s virtual isolation.
As confidential computing technologies, they are just perfect to enhance security in sensitive workloads and meet compliance needs even in managed colocation hosting.
So, if you’re ready to protect your data with the newest tech, submit a free quote request today at ServerMania!
Was this page helpful?

