What is Port Security in a Network and How Does it Work?

Do you want to protect your network? Do you want to restrict access to an unknown wired network? Or do you want to learn more about port security?
If so, then you are in the right place. In this tutorial, we are going to explain what port security is, why to use it, and how it works.
What is Port Security?
Port security is a feature in network switches that blocks unknown wired devices from gaining access to a network. Port security is a significant part of networking. By configuring port security it gives us the ability to control and restrict access to our network in order to protect the network from malicious attacks.
By default, any device would work if you connect it to the switch ports, but it may not be a good idea to leave you network vulnerable. That is why we need to use port security in order to protect our network.
Port security, as its name implies, can control the port of a switch. Port security is a port/interface based feature that the network admin can enable for each individual port on a network switch.
See also: Port speed test
How does Port Security work?
In networking, we have a term called MAC addresses which is a unique identifier assigned to devices on a network. So by using MAC addresses, port security can restrict access to a network.
The MAC addresses can be defined either statically or dynamically. When the switch detects a specific MAC address or secure MAC addresses that is valid, it would let the device connect to the network. If not, port security would go to err disabled mode and stop the device from connecting to the network.
There are two modes of restriction in port security, and those are as follows:
- MAC address based: Meaning you would specify some MAC addresses either dynamically or statically and if a device has the same secure MAC address the port security would allow it to connect.
- Maximum number of MAC addresses based: In this mode you could specify how many MAC addresses or devices could connect to the network at a given port.
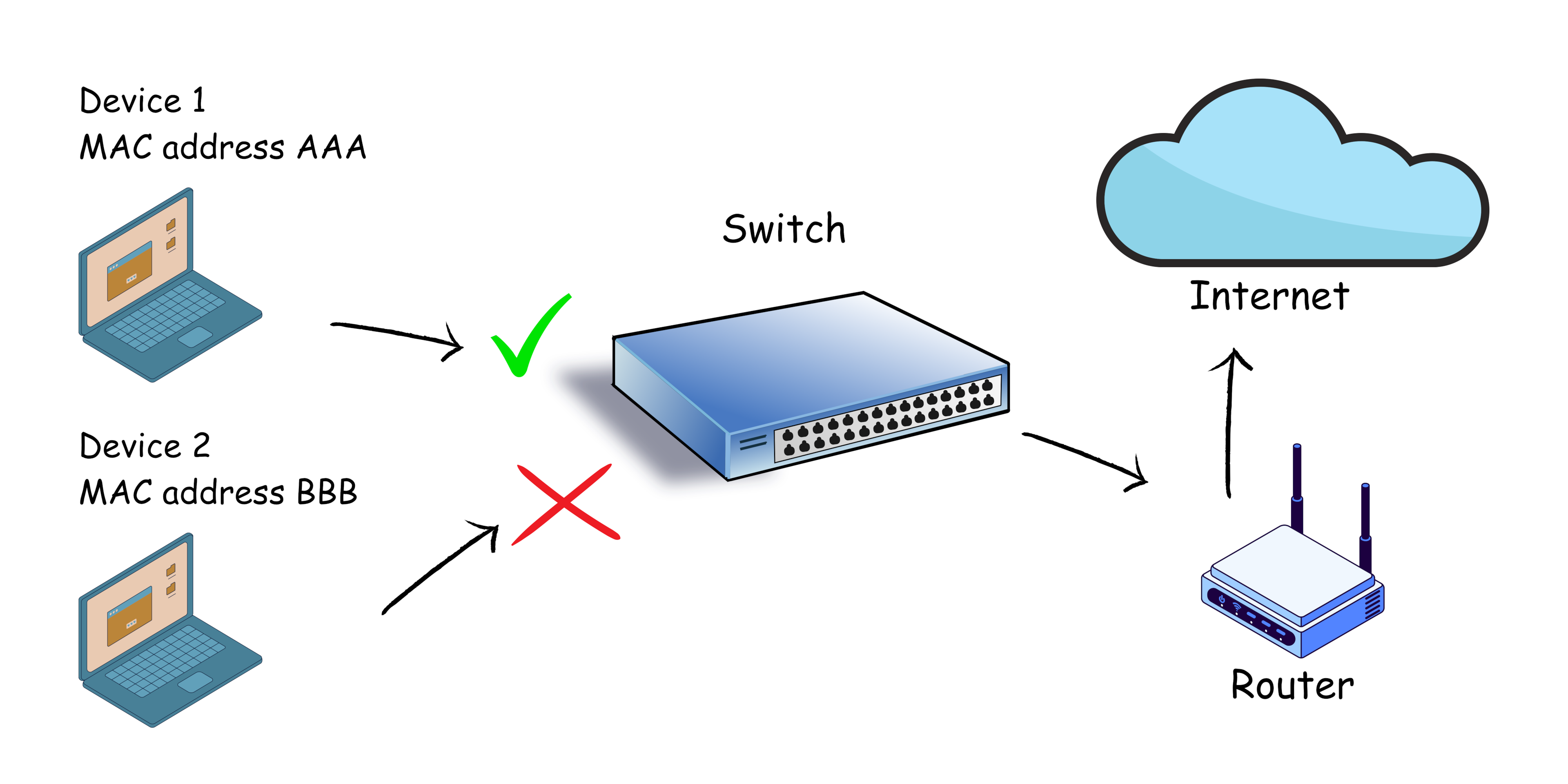
As you could see in this picture below that by implementing port security we could secure our network from unwanted devices and just allow specific MAC addresses.
Why Use Port Security?
Port security may not be an ideal option if you are setting it up on your home network with one computer, but in bigger networks where there are hundreds of users and ports, then there is a need for special security to make sure authorized devices are using the network. Thus port security helps us to secure our network from harmful attackers.
Plus port security can help us limit the traffic on our network, so that not everyone could connect to it and overload the network. Also it helps us monitor our network for any issues that may occur.
To better explain the advantages of port security let us look at a simple example.
You have a switch on your network which has around 35 ports. Some of the ports are used by your employees, but there are a many left unused. If someone with bad intentions gets his hand on your unprotected network, then you might be in a serious trouble. The attacker could perform a wide range of attacks that could harm you and your company in a lot of ways. But there is no need to fear when port security is here. By enabling port security with a few commands you are now fully secure against these types of threats.
How does Port Security Identify Valid devices
In order for port security to work it needs to get the MAC address of a device either statically or dynamically.
- Dynamically: It means whenever you enable port security, the first source MAC address that connects would be learned and identified as as secure MAC address by the port service.
- Statically: You can add custom MAC addresses to your port filter so that port security allows your devices to connect to the network with those specified MAC addresses.
Keep in mind that whenever you enable port security on a switch port, by default it will allow only a single MAC address to connect to it. If you would like to connect more devices, you could statically add new ones.
Port Security Violation Actions
What will happen if an unauthorized device connects to your network?
Well that is what port security violation actions are for. When an unauthorized device tries to gain access to a network, then a security violation occurs. By default, port security shuts down the port until it is re-enabled it once again.
When security violations occur and make the port go off, then only the admin can re-enable the port.
There are three types of violation modes:
- Shutdown: In this mode the port is shutdown after unauthorized access and it remains off until the admin re-enables it. This mode will also trigger a log message to the admin.
- Restrict: In this mode port security would not allow unauthorized devices to connect, but it would not shutdown the port either. If they tried to connect a log message would appear each time they tried to connect and the violation counter goes up one digit each time. A valid device could still use it after an unauthorized device has tried to connect.
- Protect: In this mode the switch discards the unauthorized traffic but would not turn the port off. It would not generate a log message and would not change the violation counter.
Do servers need port security?
Technically no, but if you are setting up a dedicated server on a network then you might need to have the skills to implement port security. See our cloud server hosting and hosting support page for more information about port security and managed services.
If you’re looking to choose the best server for your small business check out our Cloud Server for Small Business Guide.
Conclusion
Port security indeed is a useful feature in networking. You can easily configure port security within a few commands and start protecting your network against malicious and harmful attacks; it really is a good feature to have on your network.
On the other hand, it may be hard to maintain and afford this kind of system, so weighing the pros and cons of this setup is essential.
Next Step
Now that you have acquired some knowledge about port security and what it is used for, you can now look into setting it up yourself. We also recommend you take a look at our knowledge base to enrich your knowledge about IT and the cloud.
See our latest articles and tutorial videos, like this article on how to SSH on a Mac.
Was this page helpful?

